A Definition of statistics Encryption
Facts encryption translates information into some other form, or code, in order that best humans with get admission to to a mystery key (officially known as a decryption key) or password can examine it. Encrypted records is generally called ciphertext, at the same time as unencrypted facts is known as plaintext. Presently, encryption is one of the most popular and powerful records protection methods utilized by groups. Two principal types of data encryption exist - asymmetric encryption, also known as public-key encryption, and symmetric encryption.
The primary feature of statistics Encryption
The reason of information encryption is to defend digital data confidentiality as it's miles stored on laptop structures and transmitted the use of the internet or other pc networks. The outdated records encryption general (DES) has been changed by using current encryption algorithms that play a vital function within the protection of IT systems and communications.
These algorithms offer confidentiality and pressure key protection projects consisting of authentication, integrity, and non-repudiation. Authentication lets in for the verification of a message’s foundation, and integrity presents proof that a message’s contents have no longer modified because it become despatched. Additionally, non-repudiation ensures that a message sender can not deny sending the message.
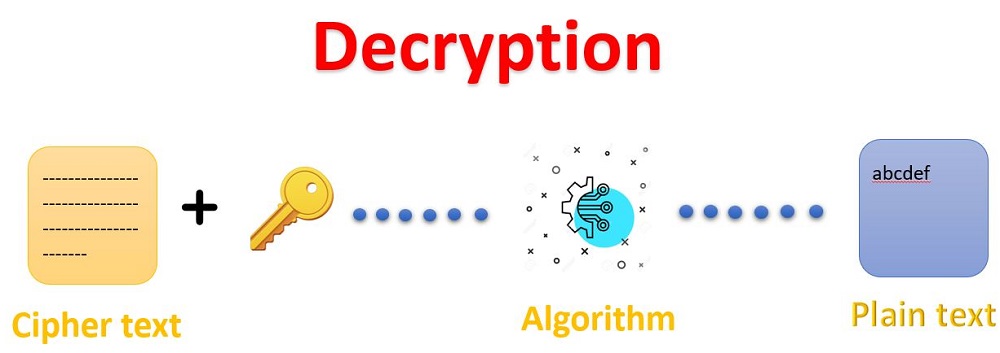
How Does Encryption paintings
Records, or plaintext, is encrypted with an encryption set of rules and an encryption key. The system consequences in ciphertext, which only may be regarded in its unique shape if it's far decrypted with the precise key.
Forms of encryption
Symmetric-key ciphers use the same mystery key for encrypting and decrypting a message or report. While symmetric-key encryption is a lot faster than uneven encryption, the sender must change the encryption key with the recipient earlier than he can decrypt it. As agencies discover themselves desiring to securely distribute and manage huge quantities of keys, maximum records encryption services have adapted and use an asymmetric set of rules to change the name of the game key after the use of a symmetric set of rules to encrypt information.
Alternatively, asymmetric cryptography, once in a while called public-key cryptography, uses special keys, one public and one personal. The general public key, because it is named, can be shared with each person, but the non-public key have to be blanketed. The Rivest-Sharmir-Adleman (RSA) algorithm is a cryptosystem for public-key encryption that is extensively used to comfy sensitive facts, mainly whilst it's miles sent over an insecure network just like the net. The RSA algorithm’s popularity comes from the truth that both the public and private keys can encrypt a message to guarantee the confidentiality, integrity, authenticity, and non-repudiability of electronic communications and data thru the use of digital signatures.
Challenges to present day Encryption
The maximum fundamental technique of attack on encryption today is brute pressure, or trying random keys till the right one is discovered. Of route, the length of the important thing determines the viable number of keys and impacts the plausibility of this sort of assault. It's miles vital to understand that encryption energy is immediately proportional to key length, but as the key length increases so do the range of resources required to carry out the computation.
Alternative strategies of breaking a cipher consist of aspect-channel assaults and cryptanalysis. Aspect-channel attacks go after the implementation of the cipher, as opposed to the real cipher itself. Those attacks generally tend to be successful if there's an error in device design or execution. Likewise, cryptanalysis method locating a weak point in the cipher and exploiting it. Cryptanalysis is more likely to arise while there is a flaw in the cipher itself.
Information Encryption solutions
Records safety answers for statistics encryption can provide encryption of gadgets, e mail, and records itself. In many cases, those encryption functionalities also are met with manage capabilities for gadgets, e-mail, and information. Corporations and agencies face the mission of protecting statistics and stopping records loss as employees use outside devices, removable media, and internet programs greater often as part of their day by day commercial enterprise approaches. Sensitive records may additionally now not be beneath the agency’s manage and safety as employees replica records to removable gadgets or add it to the cloud. As a end result, the nice statistics loss prevention answers save you statistics robbery and the advent of malware from detachable and outside gadgets in addition to web and cloud applications. So as to do so, they must additionally ensure that devices and packages are used properly and that facts is secured by using vehicle-encryption even after it leaves the enterprise.
As we referred to, electronic mail manage and encryption is some other important issue of a records loss prevention solution. At ease, encrypted electronic mail is the handiest solution for regulatory compliance, a faraway staff, BYOD, and project outsourcing. Most desirable facts loss prevention answers permit your personnel to maintain to work and collaborate via electronic mail at the same time as the software program and equipment proactively tag, classify, and encrypt sensitive statistics in emails and attachments. The first-rate statistics loss prevention answers robotically warn, block, and encrypt touchy statistics based totally on message content material and context, inclusive of person, records elegance, and recipient.
Even as information encryption may look like a frightening, complicated technique, information loss prevention software program handles it reliably each day. Information encryption does no longer ought to be some thing your organisation attempts to solve on its personal. Select a pinnacle records loss prevention software that gives statistics encryption with device, e mail, and alertness manage and rest assured that your statistics is secure.


No comments:
Post a Comment
if you have any doubts, plz let me know